A modification of Linux.Sshdkit (current version is 1.3.1) designed to steal data stored on servers running Linux. In this version, cybercriminals implemented a modified routine for generation of command and control servers' addresses.
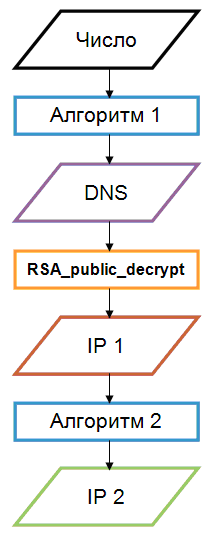
Cybercriminals also changed the command reception algorithm; that is, for command to be successfully executed, the program receives a special string, for which the hash function value is checked.
Cybercriminals use the following command and control servers:
| Second-level domain | Third-level domain IP | Modified IP |
|---|---|---|
| o8rad5ccx***r.net | 135.61.**.24 | 74.82.**.14 |
| zbqaf5zcv***x.biz | 40.11.***.226 | 211.49.***.161 |
| c0dbq5vcj***e.info | ||
| x7sbu5hcg***f.net |