SHA1:
- 61b9fba3afe6d5e7fc6d147605b8a9feb88b2080
- 73c9a813300c1a284b3b8919ea00c3327445eaf0
A Trojan for Android mobile devices written in Kotlin. Android.Click.248.origin can be distributed via Google Play under the guise of well-known applications, including, Viber, Avito, Alisa, Youla, etc.
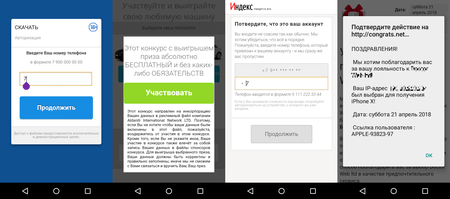
Once launched, Android.Click.248.origin checks the IP address of the infected device. Depending on a user’s location, the Trojan receives an assignment to load specific websites. On these websites, potential victims are prompted to enter the phone number necessary to receive a prize (for example, a new smartphone) or to download some applications. After entering the number, the user receives a confirmation code supposedly required to complete the application downloading process or to receive the prize. In reality, however, this code is required to confirm a subscription to a chargeable service.
If an infected device uses a mobile network to connect to the Internet, an Android device owner is subscribed to a premium service automatically after the phone number has been entered on the fraudulent website.
Cybercriminals control the Trojan via the Firebase cloud service.