SHA1 hashes:
- 2b93a1d6e570b483959eaa801c6467bf0d5e2f59
- bd9ce9d57098c5ac5d4b83feb93fdaf0d598fe15
- fffa47e23f237118eaf0b6257955a759caf66d79
Description
A malicious program which main purpose is to open web links as well as to load and display websites on-top of other apps windows. It was originally found in the app called Eye Care - Your close Eye Care Assistant (its another name is Eye Care Mini —— 急速护眼) spread through the Google Play. The trojan functionality is present in it since 2019 and was found in the versions 1.2.11, 1.2.12, and 1.2.14 of the app.
Operating routine
The trojan initializes upon the host application launch. For that, the initialization method located in the Application class is called. The malware authors have disabled the Android.Mixi.44.origin launching routine in the latest available version of the analyzed app, which is 1.2.14, but its code still remains in it.
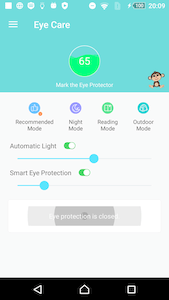
Once launched, the trojan operates in accordance with user expectations. An example of the application UI after its start is shown below:
Trojan’s program logic
Android.Mixi.44.origin uses the following services, activities and broadcast receivers:
<activity android:name="com.ad.s.cv.mg"/>
<service android:name="com.ad.s.dv.js"/>
<service android:name="com.ad.s.pa.so"/>
<receiver android:name="com.ad.s.dv.sr">
<intent-filter>
<action android:name="android.intent.action.BOOT_COMPLETED"/>
<action android:name="android.net.conn.CONNECTIVITY_CHANGE"/>
<action android:name="android.intent.action.USER_PRESENT"/>
<action android:name="android.intent.action.ACTION_POWER_DISCONNECTED"/>
<action android:name="android.intent.action.ACTION_POWER_CONNECTED"/>
</intent-filter>
</receiver>
<receiver android:name="com.ad.s.dv.r">
<intent-filter>
<action android:name="android.intent.action.PACKAGE_REPLACED"/>
<action android:name="android.intent.action.PACKAGE_ADDED"/>
<action android:name="android.intent.action.PACKAGE_REMOVED"/>
<action android:name="android.intent.action.USER_PRESENT"/>
<action android:name="android.intent.action.DOWNLOAD_COMPLETE"/>
<action android:name="android.intent.action.ACTION_POWER_CONNECTED"/>
<action android:name="android.intent.action.ACTION_POWER_DISCONNECTED"/>
<action android:name="android.intent.action.SCREEN_ON"/>
</intent-filter>
</receiver>
com.ad.s.dv.r broadcast receiver
Launches the com.ad.s.dv.js service, as well as tracks the android.intent.action.PACKAGE_ADDED and the android.intent.action.PACKAGE_REMOVED system events through which it controls which apps the user install and uninstall. The information about each event is saved to the database. Moreover, during its work the Android.Mixi.44.origin stores mrefferMap and mpaddMap hash tables in RAM.
If the information about the application installed is not present in the mrefferMap, the app’s packet name with the installation date are added to the mpaddMap database. However, if mrefferMap has this information about the app, the trojan sends an intent as shown below:
Intent i = new Intent("com.android.vending.INSTALL_REFERRER");
i.setPackage(packageName);
i.putExtra("referrer", "utm_source%vigo");
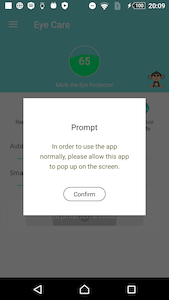
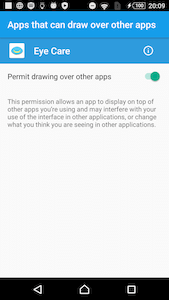
If special flag is set, the com.ad.s.dv.r broadcast receiver initializes a WebView which is placed on-top of other UI elements. In order to do so, the trojan exploits a Toast Overlay vulnerability that affects Android devices running Android OS up to version 7.1. Android.Mixi.44.origin creates AlertDialog, sets it a Toast type and places a WebView inside this pop-up dialogue. In this WebView, a website, which URL is received upon the C&C server command, is loaded.
com.ad.s.dv.sr broadcast receiver
Launches a com.ad.s.dv.js service; upon each triggering, it uploads to the C&C server 5 records from the database that stores the information about the apps installed and uninstalled by the user, as well as all the tasks successfully completed by the trojan.
com.ad.s.dv.js service
Connects to http://***.*aroom.net:9082/ovs/customer/heartBeat2.do and requests tasks to execute, as well as the configuration, including the URL where the trojan will upload the reports about completed tasks.
Uploads 5 reports to the C&C server from the database. Upon the service work is complete, it is set to run again within specified time intervals through the AlarmManager. To run the tasks, the com.ad.s.pa.so service is launched, and the task type is set in the extras attribute. With that, the service launch function can operate with more types of the tasks than the service itself in the analyzed sample.
com.ad.s.pa.so service
Executes main commands.
The ACTION_TYPE_USER_REG command ― to register the infected device in the attackers’ network. The following information is sent to the http://***.*aroom.net:9082/ovs/customer/reg.do C&C server:
- SID, UID ― current user ID assigned by the trojan;
- androidId ― a unique device ID (the android.provider.Settings.Secure.getString(ctx.getContentResolver(), "android_id") value is sent);
- gid ― Google advertising ID;
- OSVersion ― an OS version (the android.os.Build.VERSION.RELEASE value is sent);
- version ― a version of the trojan app;
- gpver ― a version of the Play Store app installed on the device;
- wbver ― a version of the WebView.
In response, the Android.Mixi.44.origin receives the SID and the UID user IDs set by the server, saves them and launches the com.ad.s.dv.js service. By default, the values of the IDs received from the C&C server are empty.
The ACTION_TYPE_PUSH_MSG command ― to load and display web pages on-top of other app’s windows, using the Toast Overlay vulnerability mechanism described earlier.
The ACTION_TYPE_OFFER_GET command ― to covertly open the URLs received from the C&C server (a clicker functionality). The task received from the C&C server contains a URL that trojan visits to receive the list of additional links to open. For each such link, the com.ad.s.cv.mg activity is launched within specified time intervals. The activity receives the specific window parameters that make it invisible to the user. In this activity, a WebView is created. In this WebView, the trojan opens a targeted URL.
If this URL redirects to the software page in the Play Market app, the trojan adds this software’s packet name to the mrefferMap table. Herewith, if the com.ad.s.dv.r broadcast receiver will receive the information that this particular application later on, the following intent will be sent:
Intent i = new Intent("com.android.vending.INSTALL_REFERRER");
i.setPackage(packageName);
i.putExtra("referrer", "utm_source%vigo");
However, if this application has been installed recently and the information about it is available in the mpaddMap table list, the following intent will be immediately sent:
Intent intent = new Intent("com.android.vending.INSTALL_REFERRER");
intent.setPackage(packageName);
intent.putExtra("referrer", referrer);
With that, the packageName and the referrer parameters are obtained from the URL led to the app’s page in the Play Store application.
This way, the Android.Mixi.44.origin tries to trick the analytics service, giving the credit for the app installation performed by the user to cybercriminals.
The news about the Android.Mixi.44.origin
Read more about the Toast Overlay vulnerability