Packer: absent
Compilation date: absent
SHA1 hash:
- 8d1b7d738c4c0f0aba5c25b096b54b3fc20e5643
Description
RAT malware that operates in the 32-bit and 64-bit versions of Microsoft Windows operating systems. The studied sample is an MSI package with pre-configured remote control parameters created with MSI Configurator from the Remote Utilities Viewer. It spreads within the self-extracting 7z-dropper (52c3841141d0fe291d8ae336012efe5766ec5616) via phishing emails. The backdoor is designed to remotely control the infected computer.
Operating routine
Content of the dropper:
- host6.3_mod.msi (a pre-configured MSI package)
- installer.exe (5a9d6b1fcdaf4b2818a6eeca4f1c16a5c24dd9cf), signed with a valid digital signature
.>sigcheck.exe -a installer.exe
Verified: Signed
Signing date: 4:20 08.05.2015
Publisher: Usoris Systems
Company: Usoris Systems LLC
Description: Remote Utilities
Product: Remote Utilities
Prod version: 6.3.0.1
File version: 6.3.0.1
MachineType: 32-bit
Binary Version: 6.3.0.1
Original Name: n/a
Internal Name: Remote Utilities part
Copyright: Copyright © 2015 Usoris Systems LLC All rights reserved.
Comments: Modified by an unpaid evaluation copy of Resource Tuner Console 2 (www.heaventools.com)
Entropy: 6.599
Self-extracting archive script:
;!@Install@!UTF-8!
RunProgram="hidcon:installer.exe /rsetup"
GUIMode="2"
;!@InstallEnd@!
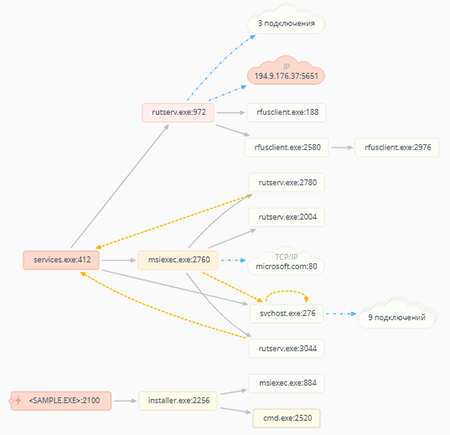
After unpacking, the dropper launches the installer.exe, which in turn initiates installation of a pre-configured MSI package. The installer extracts and silently installs the Remote Utilities program. After installation, it sends a notification to the C&C server.
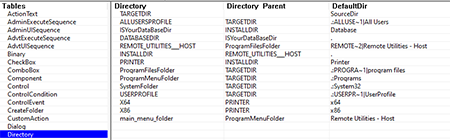
The MSI package contains all the necessary parameters for silently installing the Remote Utilities. Installation is performed in Program Files\Remote Utilities - Host in accordance with the Directory table.
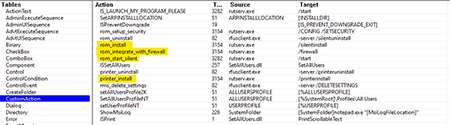
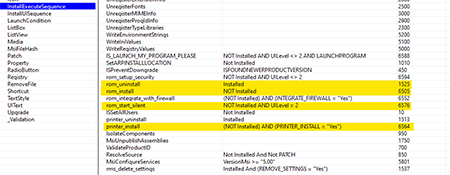
According to the CustomAction table, the msiexec.exe installer launches the main module of the Remote Utilities package rutserv.exe with various parameters that provide:
- Silent installation,
- The addition of firewall rules, and
- Service start up.
The sequence is defined by the value of the Sequence field for the corresponding action in the InstallExecuteSequence table.
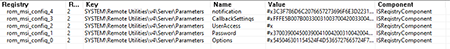
Connection parameters and settings are added in the HKLM\Remote Utilities\v4\Server\Parameters registry key. The parameter values are stored in the Registry table:
The CallbackSettings parameter contains the address of the server to which the InternetID is sent for direct connection:
[{317B3E33-A4DE-4EC5-A954-28C2B8AAF218}]
internal_connection_id=--
host=194.9.176.37
port=5651
text_message=
auto_connect=1
status=2
display_name=194.9.176.37
disallow_tray_connect=0
append_computer_name=1
[{13BD64A6-87CB-4065-9AF6-8F9427F3A2E1}]
internal_connection_id=--
host=194.9.176.38
port=5651
text_message=
auto_connect=1
status=2
display_name=194.9.176.38
disallow_tray_connect=0
append_computer_name=1
[{D6FE29FE-11E2-4492-B662-8414706755DF}]
internal_connection_id=--
host=194.9.176.38
port=81
text_message=
auto_connect=1
status=2
display_name=194.9.176.38
disallow_tray_connect=0
append_computer_name=1
[{B7C30242-C4A1-4767-992A-37CC3AA568F6}]
internal_connection_id=--
host=194.9.176.39
port=81
text_message=
auto_connect=1
status=2
display_name=194.9.176.39
disallow_tray_connect=0
append_computer_name=1