A multicomponent malicious program designed to steal information stored in applications used by drugstores and pharmaceutical companies to purchase drugs. This version’s main purpose is to steal data from the FM_client.exe application (AIAS INPRO-FarmRynok (“АИАС ИНПРО-ФармРынок”) by Information Technologies (“Информационные Технологии”)). The malware contains several modules.
pexec.dll
A module containing the Trojan’s drivers and the payload. From its body, the module decrypts main components and checks if there is a mutex available (if not, the Trojan creates it).
Global\{3D5A1694-CC2C-4ee7-A3D5-A879A9E3A62A}After that, he malicious program extracts the encrypted driver from the .cdata section and saves it under the following name:
%SYSTEM32%\drivers\isaPnpPrt.cfgThen the main module extracts two encrypted files (the backdoor’s driver and module) from the .bdata section, decrypts and unpacks them, and saves the driver under the following name on the disk:
%SYSTEM32%\drivers\isaPnpPrt.sysThe backdoor is saved under the following name:
%SYSTEM32%\isaPnpPrt.inf_x86_neutral_1c30fe3e981e1595The Trojan saves the parameters necessary for its normal work in the system registry.
REGEDIT4
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\isaPnpPrt]
"ImagePath"="system32\\drivers\\isaPnpPrt.sys"
"DisplayName"="isaPnpPrt"
"Group"="Boot Bus Extender"
"Type"=dword:00000001
"Start"=dword:00000001
"ErrorControl"=dword:00000000
"ID"="21d9d915f9671_743bcf967336482db184f3c64db39b12"
"Desc"="C:\\WINDOWS\\system32\\isaPnpPrt.inf"
"DriverPackageIdPkg"="\\??\\C:\\WINDOWS\\system32\\isaPnpPrt.inf_x86_neutral_1c30fe3e981e1595"
"RulesData"=hex:02,00,00,00,a6,00,5c,00,44,00,65,00,76,00,69,00,63,00,65,00,5c,\
00,48,00,61,00,72,00,64,00,64,00,69,00,73,00,6b,00,56,00,6f,00,6c,00,75,00,\
6d,00,65,00,31,00,5c,00,57,00,49,00,4e,00,44,00,4f,00,57,00,53,00,5c,00,73,\
00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,69,00,73,00,61,00,50,00,\
6e,00,70,00,50,00,72,00,74,00,2e,00,69,00,6e,00,66,00,5f,00,78,00,38,00,36,\
00,5f,00,6e,00,65,00,75,00,74,00,72,00,61,00,6c,00,5f,00,31,00,63,00,33,00,\
30,00,66,00,65,00,33,00,65,00,39,00,38,00,31,00,65,00,31,00,35,00,39,00,35,\
00,00,00The driver is run using the NtLoadDriver function.
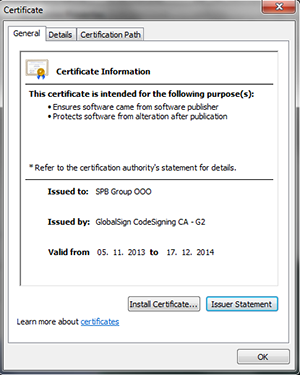
One of two drivers has the size of about 8 KB and is usually stored in the file with the name rpcssprt.sys or in the file isaPnpPrt.sys. The main purpose of this driver is to load another driver with the same name but with the different extension (.cfg) into the memory of the infected computer. If the driver succeeds in opening the file containing the payload, this file is decrypted, unpacked, and loaded into the memory. Both files have the digital certificate registered in the name of SPВ Group LLC (“SPВ Group OOO”).
The properties of isaPnpPrt.sys claim this file to be an ATAPI driver by Microsoft Corporation.
The main driver creates a new virtual device \\.\{41C4774D-A453-4330-8C6C-FEBEACC85D7E} that can execute the following commands:
- 0x220008—delete the driver from the disk and the corresponding data from the registry;
- 0x22000C—get the Trojan’s ID (the ID value is extracted from the registry);
- 0x220010—get the path to the configuration file;
- 0x220014—get the path to the Trojan’s main body (“DriverPackageIdPkg”);
- 0x220018—acquire elevated privileges for the current thread (it is used by the Trojan’s main module before launching the files downloaded from the network);
- 0x22c004—get and reset the counter of the processes in which the malicious module was incorporated.
In fact, the driver serves only one main purpose—to embed the payload into the explorer.exe and svchost.exe processes.
fmauto.dll, fmauto2.dll
A payload that steals information from online drug ordering systems. This component extracts the file containing purchase information from the online application, generates an archive, creates a password, and forwards the archive to the server. The archive can contain the following data:
info.txt
Аптека-******* г.Ростов-на-Дону.csv
*******-Фарма г.С-Петербург.csv
******-Ростов.csv
***** г.Волгоград.csv
**** г.Краснодар.csv
***** (*****фармация) Ростовский филиал.csv
*** ****** г.Ростов-на-Дону.csvThe info.txt file usually contains the information regarding the infected computer, for example, as follows:
Client Name: ООО "****-Фарм"
Date: 02.04.2014
OS Version: Windows XP
Client Version: 1.5.160.0
Module Version: 4.3
COMPNAME: ***SRV
Date3: 02.04.2014
PC TIME: 02.04.2014 13:11:20In turn, each CSV file contains the data regarding drug purchases and prices, for example, as follows:
Date: 02.04.2014
Firm: Аптека-******* г.Ростов-на-Дону
Скидки-наценки: Конечные цены!
Код;Цена;Минимальная цена;Остаток;
27484;204,36;9 месяцев Омегамама капс. 0.7г N30;Отечественные лекарства Польша;166,19;9;
29772;1343,3;Авандамет табл. п.п.о. 2мг/500мг N56;GlaxoSmithKline Traiding Испания;1181,91;5;
21385;310,45;Адвантан мазь 0.1% туба 15г;Bayer Consumer Италия;273,1;347;
26518;59,28;Адрианол капли назальн. фл.-кап. 10мл;Actavis Сербия;52,53;93;
15955;26,59;Азитромицин капс. 250мг N6;Вертекс ЗАО Россия;23,8;3530;
33329;112,41;Азитромицин табл. п.п.о 500 мг N3;Березовский фармацевтический з Россия-Македония;99,3;269;
…The payload executes the requests that look as follows:
select KPP, FDATE, MAINNAME from ZAKAZ1 where FDATE between ****
select KPP, FIRM, KOL, KOD, CENA from ZAKAZ2 where KPP=***The requests are used for extracting the information from clients’ databases.
exist.dll
A module designed to troubleshoot any errors in the functioning of the malicious program.
isaPnpPrt.inf_x86_neutral_1c30fe3e981e1595
The backdoor’s main module. Using a special algorithm, it generates a name of the command and control server and then sends this server POST requests containing the data on the module’s current configuration.
a=ZAKAZ_B4DF7611035CBAD4&b=BASE64(RC4(label=rnd&ver=26&t=CFG&d=RC4([common]\r\ndefdll=0F95DA37\r\n)))Where “a” stands for the generated key, “label” and “ver” stand for the Trojan’s version, “t” stands for the command, and “BASE64” and “RC4” stand for the data encrypted with these algorithms.
If the server successfully receives the data, it sends the status 200 to the Trojan. Then the backdoor considers this server to be a command and control one.
The main module can execute the following commands:
- mod—install the module;
- delmod—delete the module;
- dande—update Win32.Dande, download the file, and, if necessary, decrypt, save, and run it;
- setopt—set options.
The module can send the following reports to the command and control server:
- MODSCS—report on the successful module installation. After this report is received, configuration with the installed module at the t=ping command is no longer sent.
- DANDE_INST_SCS—download and install the module at the dande command.
- DELMODSCS—delete the module.
- RESULT—send the work results of the downloaded module.
Module installation
To install the modules, the backdoor requests the configuration from the command and control server.
a=ZAKAZ_B4DF7611035CBAD4&b=BASE64(RC4(label=rnd&ver=26))In return, it receives the configuration that looks as follows:
BASE64(RC4(t=mod&n=fmauto.dll&f=Routine&p=none&ps=explorer.exe&d=RC4(file)))where
“file” stands for the module library,
“t=mod” stands for the module installation command,
“n” stands for the module name,
“f” stands for the name of the exported function,
“p” stands for the function parameters,
“d” stands for the encrypted binary data.
Using the received data, the backdoor generates a new configuration file C:\windows\temp\ as follows:
[common]
domnum=1
domsubnum=0
timeHI=30363270
timeLO=-1049525216
[ff.dll]
func=Routine
param=none
path=C:\Windows\SERVIC~2\NETWOR~1\AppData\Local\Temp\mAAEE.tmp
procs=explorer.exe
[results]
[p1.dll]
func=Routine
param=none
path=C:\Windows\SERVIC~2\NETWOR~1\AppData\Local\Temp\mD5F3.tmp
procs=explorer.exe
[fm1.dll]
func=Routine
param=none
path=C:\Windows\SERVIC~2\NETWOR~1\AppData\Local\Temp\mB04B.tmp
procs=explorer.exe
[f1.dll]
func=Routine
param=none
path=C:\Windows\SERVIC~2\NETWOR~1\AppData\Local\Temp\m3AC1.tmp
procs=explorer.exe
[executed]
ff.dll=1The Trojan encrypts the executable file and saves it to the C:\windows\temp\ folder. Then it sends the report on the successful module installation to the command and control server.
a=ZAKAZ_B4DF7611035CBAD4&b=BASE64(RC4(label=rnd&ver=26&t=MODSCS&n=fmauto.dll))The malware periodically scans the contents of the С:\windows\temp folder and loads the modules into the memory.