Steals confidential information from customers of Kookmin Bank in South Korea. Spread in the guise of a legitimate banking application, it uses the same title and icon.
After its successful launch, it demonstrates a fake notification informing the user that the mobile device is protected by the anti-virus AhnLab V3 Mobile Plus—the legitimate banking application behaves exactly this way and checks if the handheld is protected.
 |

|
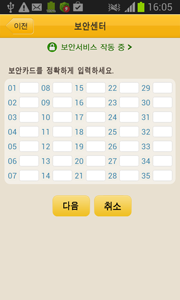
The malicious program checks if NPKI-certificates are present in the memory card's root folder and if found, places them in zip-archives, which are saved next to the original filess, and then displays information about the found files.
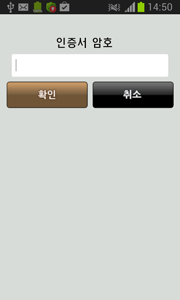
When the user taps on an item on the list, Android.Banker.26.origin prompts them to enter a password for the corresponding certificate.
The malware uses the following method to verify entered passwords: if the password is longer than or equal to six characters, it informs the victim about an error and prompts them to re-enter the password, while temporarily storing the previous value (if the input value is less than six characters, it will not be saved). If the re-entered value coincides with the previous one and is longer than six characters Android.Banker.26.origin proceeds to the next step of collecting confidential information. In particular, the malicious program prompts the user for the following credentials:
- name;
- id_first – id_second;
- account;
- account password.
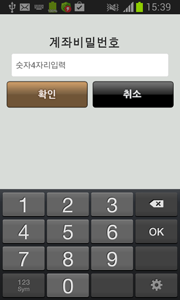
If the user selects the last option—enter a password—the Trojan displays a separate field that accepts numeric values of no fewer than four characters.
Once the required data is entered, Android.Banker.26.origin invites its victim to input their credit card number.
All the confidential information collected by the malware, including certificates and the IMEI, is sent to a remote server located at http://xxx.xx.177.105:80/v/ . This information is transmitted in JSON format and arranged as follows:
{:"clientId" :
"accountName" :
"accountNo" :
"accountPsw" :
"bkType" :
"certPath" :
"card" :
"transPsw" :
"certPsw" :
"personIdFirst" :
"personIdSecond" :
"fileName" :}