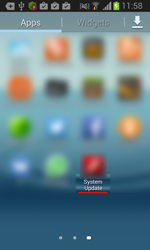
This is a Trojan for Android mobile devices. It is used by cybercriminals to steal users' confidential information and money from bank and mobile accounts, associated with those devices. The Trojan can be distributed in the guise of system update.
Once Android.BankBot.34.origin has been installed on the target mobile device, it places the icon on the home screen that is similar to the icon of a popular legitimate application. Later, the malware will remove its previously created icon if the Trojan is launched by the owner of the infected mobile device. If the user does not activate the malicious program, this icon remains on the home screen. The Trojan can start itself automatically having booted with the operating system (to do this, it uses standard monitoring of system event android.intent.action.BOOT_COMPLETED).
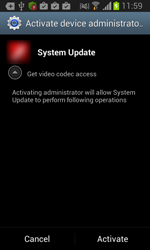
When launched, Android.BankBot.34.origin prompts the user to grant it administrative privileges.
Unauthorized access to confidential information
The Trojan tracks user's activity and waits for the following mobile applications to be launched:
- Google Play (com.android.vending);
- Google Play Music (com.google.android.music);
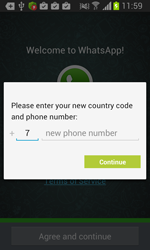
- WhatsApp (com.whatsapp);
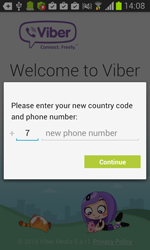
- Viber (com.viber.voip);
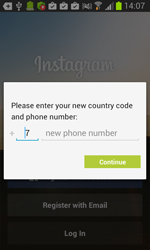
- Instagram (com.instagram.android);
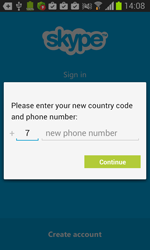
- Skype (com.skype.raider);
- VK (com.vkontakte.android);
- "Одноклассники" (ru.ok.android);
- Facebook (com.facebook.katana);
- Gmail (com.google.android.gm);
- Twitter (com.twitter.android).
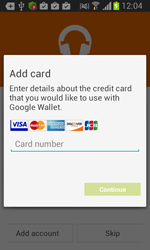
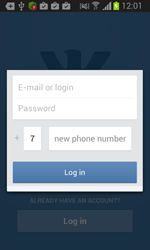
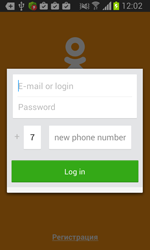
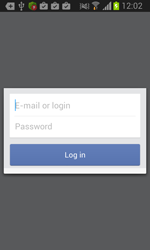
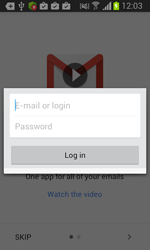
Once one of these programs is being launched, Android.BankBot.34.origin displays a phishing dialogue box on top of the application's interface to prompt users to divulge their confidential information—login and password, phone number, or credit card information. The received data in JSON format (JavaScript Object Notation) is transmitted to the command and control server. For example, the credit card information looks as follows:
JSONObject v3 = new JSONObject();
v3.put("type", "card information");
JSONObject v1 = new JSONObject();
v1.put("number", card.getNumber());
v1.put("month", card.getMonth());
v1.put("year", card.getYear());
v1.put("cvc", card.getCvc());
v3.put("card", v1);
JSONObject v0 = new JSONObject();
v0.put("first name", address.getFirstName());
v0.put("last name", address.getLastName());
v0.put("street address", address.getStreetAddress());
v0.put("city", address.getCity());
v0.put("country", address.getCountry());
v0.put("zip code", address.getZip());
v0.put("phone", address.getPhone());
v3.put("billing address", v0);
JSONObject v2 = new JSONObject();
v2.put("vbv password", info.getVbvPass());
v3.put("additional information", v2);
v3.put("code", v5.getString("APP_ID", "-1"));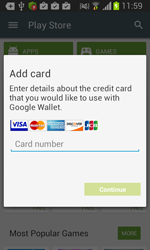 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
Communication with the command and control server and execution of issued commands
To transmit the stolen information to cybercriminals as well as to receive commands, Android.BankBot.34.origin connects over the TOR network to its command and control server at http://[xxxxxxxxx]wxnoyew.onion/. The Trojan's ability to work with anonymous communication protocol is ensured through the use in the code of Android.BankBot.34.origin fragments of an org.torproject.android legitimate application. If the main server is not available, the Trojan uses the alternate command and control server at http://[xxxxx]panel.ru/send.php.
During the first session with the remote center, the Trojan logs the infected mobile device, passing its basic information (the IMEI, the model name, the mobile number, the OS version, etc.):
JSONObject v1 = new JSONObject();
try {
v1.put("type", "device info");
v1.put("phone number", Utils.getPhoneNumber(context));
v1.put("country", Utils.getCountry(context));
v1.put("imei", Utils.getIMEI(context));
v1.put("model", Utils.getModel());
v1.put("sms", new JSONArray(Utils.readMessagesFromDeviceDB(context)));
v1.put("operator", Utils.getOperator(context));
v1.put("os", Utils.getOS());
v1.put("client number", "10");Having received the command from the server, Android.BankBot.34.origin can perform the following actions:
- Start or stop intercepting inbound and outbound SMS;
- Send a USSD-query;
- Black list a specific number, so that all messages from that number are concealed from the user (by default, the list includes customer service numbers of certain mobile operators, of a well-known Russian bank’s online banking system, and of a popular payment platform);
- Clear the black list;
- Forward information about the applications installed on the device to the remote server;
- Send an SMS;
- Relay the malware’s ID to the server;
- Display a dialogue box or a message in accordance with parameters, transmitted by the C&C server (e.g., a server instruction can specify the text to be displayed on the screen, the number of input fields, etc.).