SHA1:
- 0c0282e4edd167ae89b6866b42c1c48f8a374157
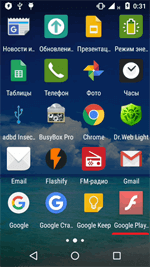
A banking Trojan for Android that steals login credentials from online banking user accounts together with money from user bank accounts. In addition, Android.BankBot.136.origin can lock the home screen of infected devices and delete all user information restoring all default settings. The Trojan is distributed under the guise of such benign applications as Adobe Flash Player, Google Play and others.
Once launched, Android.BankBot.136.origin prompts a user to grant it root privileges to remain in the system as long as possible. If the Trojan gets root privileges, it can be removed only by anti-virus software.
The Trojan registers an infected mobile device and waits a reply from the command and control server after Android.BankBot.136.origin has sent the POST request that looked as follows:
POST http://******ink.net/012/get.php HTTP/1.1
Content-Length: 360
Content-Type: application/x-www-form-urlencoded
Host: ******ink.net
Connection: Keep-Alive
User-Agent: Apache-HttpClient/UNAVAILABLE (java 1.4)
The request sends the following information:
- A unique ID generated by the Trojan;
- IMEI identifier;
- Current system language;
- Mobile network operator;
- OS version;
- Mobile device model;
- Cell phone number.
The Trojan may receive the following commands:
- intercept_down – start intercepting SMS messages (for devices running Android version older than 4.4);
- intercept_down_off – stop intercepting SMS messages;
- send_sms – send an SMS to a specified number;
- delivery_send – send SMS messages to all contact list numbers;
- apiserver – change the address of the command and control server;
- appmass – send an MMS message (in the last versions of the Trojan, this function was not implemented);
- UpdateInfo – send information about applications installed on the C&C server;
- adminPhone – change the phone number used to send SMS messages that repeat commands;
- kill_on – set a password on ScreenLock, turn sound off, and lock the home screen;
- kill_off – clear the password from ScreenLock, turn soun on, and unlock the home screen;
- upload_sms – upload incoming messages to the C&C server;
- notification – display a notification whose content is specified in the command;
- intercept_up – start intercepting SMS messages (for devices running Android 4.4 and higher);
- intercept_up_off – stop intercepting messages;
- Wipe – restore default settings (factory reset);
- callredirect_on – enable forwarding of all incoming calls;
- callredirect_off – disable forwarding of all incoming calls;
- cleanON – assign the Trojan as a default SMS manager;
- cleanOFF – assign a standard application as a default SMS manager;
- check_manager_status – check what application is a default SMS manager;
- domenlist – add an address of an additional C&C server;
- browserrestart, browserappsupdate – commands TBD.
An example of a message that is used by the Trojan to lock a device;
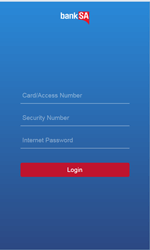
Stealing authentication information to access mobile banking services
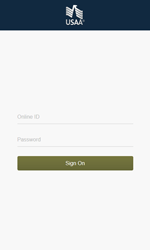
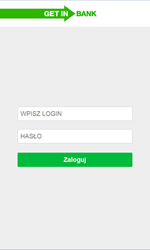
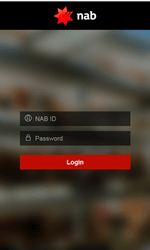
Android.BankBot.136.origin monitors launch of banking applications and then displays a fraudulent input form for entering login credentials on top of the running application. The entered data is then sent to the cybercriminals. Below, you can see an example of phishing dialogs that can be shown by the Trojan:
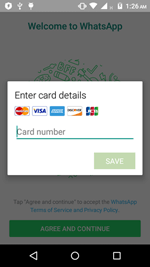
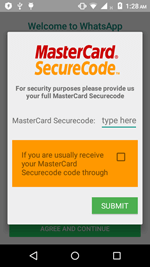
Stealing bank card information
Android.BankBot.136.origin attempts to steal user bank card information by tracking the launch of the following applications:
- com.android.vending;
- com.android.gallery3d;
- jp.naver.line.android;
- com.android.calendar;
- com.android.calendar;
- com.skype.raider;
- com.facebook.orca;
- com.facebook.katana;
- com.snapchat.android;
- com.instagram.android;
- com.viber.voip;
- com.whatsapp;
- com.twitter.android.
Once one these programs is launched, Android.BankBot.136.origin displays a phishing form demanding to enter a bank card information. For example:
This information is then sent to the C&C server.
Resistance to anti-virus software and service utilities
Some versions of Android.BankBot.136.origin can block several anti-virus programs and service utilities that can hinder the Trojan’s operation. The Trojan blocks the following software programs:
- com.cleanmaster.security;
- com.cleanmaster.mguard;
- com.piriform.ccleaner;
- com.cleanmaster.mguard_x86;
- com.cleanmaster.sdk;
- com.cleanmaster.boost;
- com.drweb;
- com.qihoo.security;
- com.kms.free;
- com.eset.ems2.gp;
- com.qihoo.security.lite;
- com.symantec.mobilesecurity;
- com.dianxinos.optimizer.duplay.
Names of banking applications attacked
Android.BankBot.136.origin monitors a launch of the following banking applications:
- RBC | CM – me.doubledutch.rbccapitalmarkets;
- Wells Fargo Mobile – com.wf.wellsfargomobile;
- U.S. Bank Access Online Mobile – com.usb.cps.axol.usbc;
- USAA Mobile – com.usaa.mobile.android.usaa;
- Union Bank Mobile Banking – com.unionbank.ecommerce.mobile.android;
- TransferWise Money Transfer – com.transferwise.android;
- TD Bank (US) – com.tdbank;
- TD (Canada) – com.td;
- SunTrust Mobile App – com.suntrust.mobilebanking;
- PNC Mobile – com.pnc.ecommerce.mobile;
- PayPal – com.paypal.android.p2pmobile;
- Western Union – Paybybank – com.paybybank.westernunion;
- Skrill – com.moneybookers.skrillpayments;
- J.P. Morgan Mobile – com.jpm.sig.android;
- Bank of America – com.infonow.bofa;
- My Premier Credit Card – com.firstpremier.mypremiercreditcard;
- CNB Mobile Banking – com.fi9228.godough;
- Discover Mobile – com.discoverfinancial.mobile;
- Credit Karma – com.creditkarma.mobile;
- Bitcoin Wallet – Coinbase – com.coinbase.android;
- Fifth Third Mobile Banking – com.clairmail.fth;
- Citi Mobile® – com.citi.citimobile;
- CIBC Mobile Banking® – com.cibc.android.mobi;
- Chase Mobile – com.chase.sig.android;
- Amex Mobile – com.americanexpress.android.acctsvcs.us;
- National Bank Application – ca.bnc.android;
- CommBank – com.commbank.netbank;
- Westpac Mobile Banking – org.westpac.bank;
- St.George Mobile Banking – org.stgeorge.bank;
- NAB – au.com.nab.mobile;
- ING DIRECT Australia Banking – au.com.ingdirect.android;
- Bankwest – au.com.bankwest.mobile;
- BankSA Mobile Banking – org.banksa.bank;
- BAWAG P.S.K. – at.bawag.mbanking;
- easybank – at.easybank.mbanking;
- ErsteBank/Sparkasse netbanking – at.spardat.netbanking;
- Volksbank Banking – at.volksbank.volksbankmobile;
- Bank Austria MobileBanking – com.bankaustria.android.olb;
- Raiffeisen ELBA – com.isis_papyrus.raiffeisen_pay_eyewdg;
- Meine Bank – com.db.mm.deutschebank;
- ING-DiBa Banking + Brokerage – com.ing.diba.mbbr2;
- DKB-pushTAN – com.starfinanz.mobile.android.dkbpushtan;
- Sparkasse+ – com.starfinanz.smob.android.sbanking;
- Sparkasse – com.starfinanz.smob.android.sfinanzstatus;
- Online-Filiale – de.adesso.mobile.android.gad;
- comdirect mobile App – de.comdirect.android;
- Commerzbank – de.commerzbanking.mobil;
- Consorsbank – de.consorsbank;
- DKB-Banking – de.dkb.portalapp;
- VR-Banking – de.fiducia.smartphone.android.banking.vr;
- ING-DiBa Kontostand – de.ing_diba.kontostand;
- Postbank Finanzassistent – de.postbank.finanzassistent;
- Santander Bank MobileBanking – mobile.santander.de;
- Crédit Mutuel de Bretagne – com.arkea.android.application.cmb;
- Crédit Mutuel Sud Ouest – com.arkea.android.application.cmso2;
- Boursorama Banque – com.boursorama.android.clients;
- Centre France – com.cacf.MonCACF;
- Banque – com.caisseepargne.android.mobilebanking;
- CIC – com.cic_prod.bad;
- Crédit Mutuel – com.cm_prod.bad;
- La Banque Postale – com.fullsix.android.labanquepostale.accountaccess;
- Groupama toujours là – com.groupama.toujoursla;
- ING Direct France – com.IngDirectAndroid;
- Mes Paiements – com.lbp.peps;
- MACIF Assurance et Banque – com.macif.mobile.application.android;
- Crédit du Nord – com.ocito.cdn.activity.creditdunord;
- Mon AXA – fr.axa.monaxa;
- Cyberplus – fr.banquepopulaire.cyberplus;
- Cyberplus PRO – fr.banquepopulaire.cyberplus.pro;
- Ma Banque – fr.creditagricole.androidapp;
- LCL pour mobile – fr.lcl.android.customerarea;
- Groupama Banque Mobile – fr.lemonway.groupama;
- L'Appli Société Générale – mobi.societegenerale.mobile.lappli;
- Mes Comptes BNP Paribas – net.bnpparibas.mescomptes;
- Alior Mobile – com.comarch.mobile;
- Getin Mobile – com.getingroup.mobilebanking;
- Citi Handlowy – com.konylabs.cbplpat;
- Bank Pekao – eu.eleader.mobilebanking.pekao;
- Mobilny Bank – eu.eleader.mobilebanking.raiffeisen;
- BZWBK24 mobile – pl.bzwbk.bzwbk24;
- BZWBK24 mobile (tablet) – pl.bzwbk.mobile.tab.bzwbk24;
- eurobank mobil pl.eurobank;
- INGMobile – pl.ing.ingmobile;
- mBank PL – pl.mbank;
- IKO – pl.pkobp.iko;
- Bank Millennium – wit.android.bcpBankingApp.millenniumPL;
- Akbank Direkt – com.akbank.android.apps.akbank_direkt;
- QNB Finansbank Cep Şubesi – com.finansbank.mobile.cepsube;
- Garanti Cep – Mobil Bankacılık – com.garanti.cepsubesi;
- İşCep – com.pozitron.iscep;
- Halkbank Mobil – com.tmobtech.halkbank;
- VakıfBank Mobil Bankacılık – com.vakifbank.mobile;
- Yapı Kredi Mobil Bankacılık – com.ykb.android;
- Ziraat Mobil – com.ziraat.ziraatmobil.